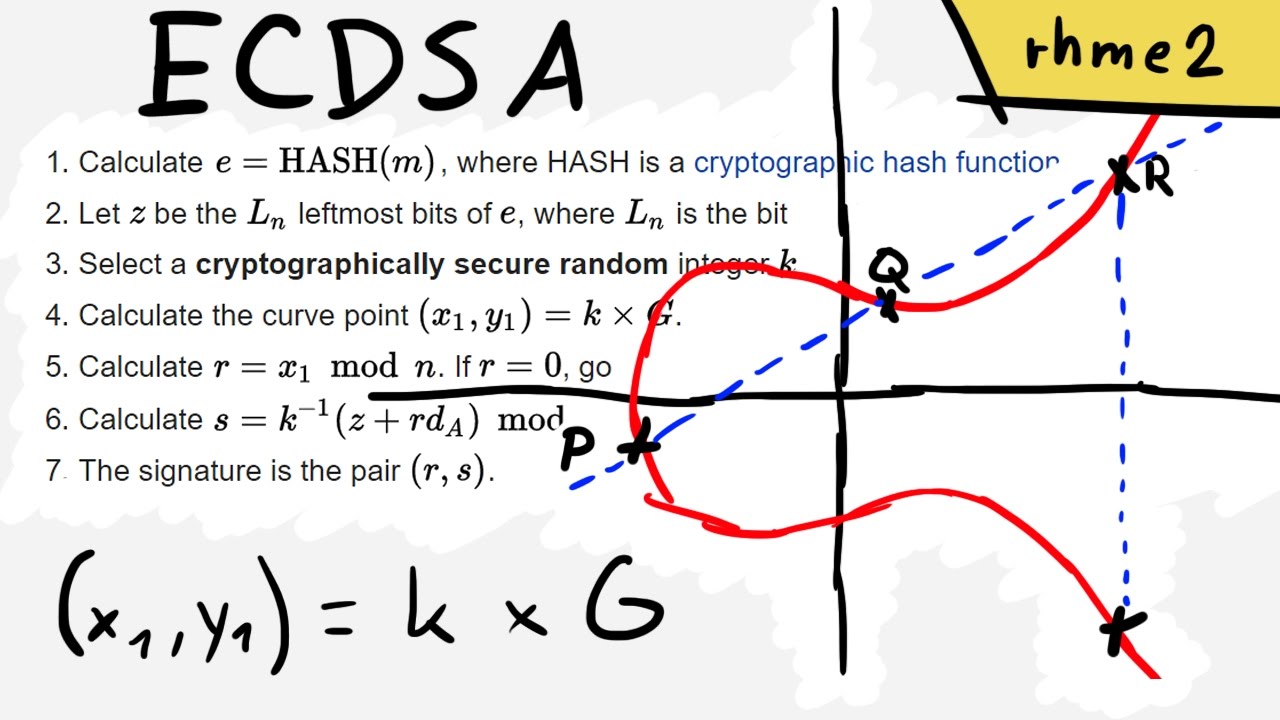
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150) - YouTube
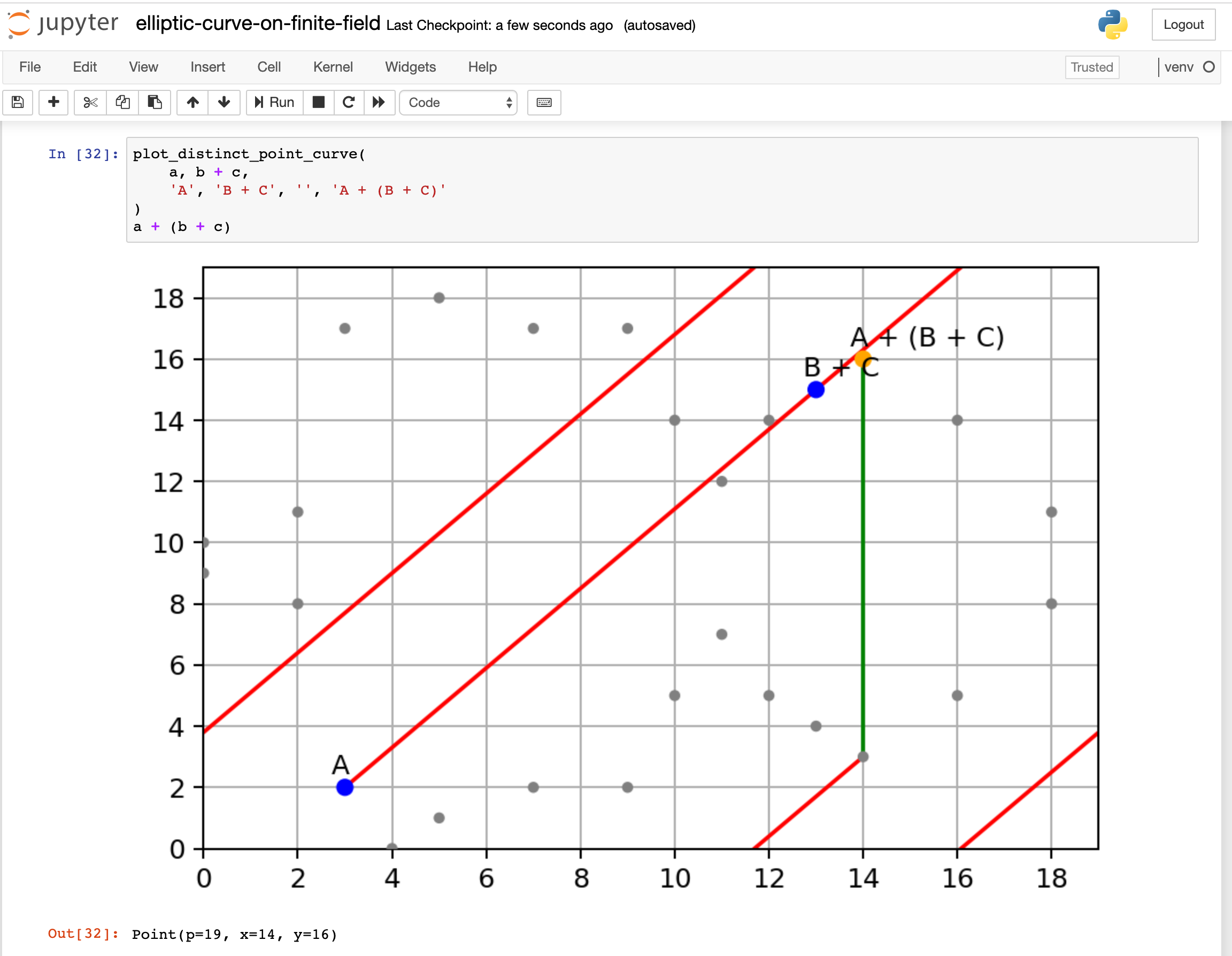
GitHub - j2kun/elliptic-curve-diffie-hellman: Python code for the post "Elliptic Curve Diffie-Hellman"
GitHub - kanika2296/elliptic-curve-diffie-hellman: Implemented in python , Elliptic-curve Diffie–Hellman (ECDH) is a key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, to establish a shared secret over

Imperfect Forward Secrecy: How Diffie-Hellman Fails in Practice | January 2019 | Communications of the ACM

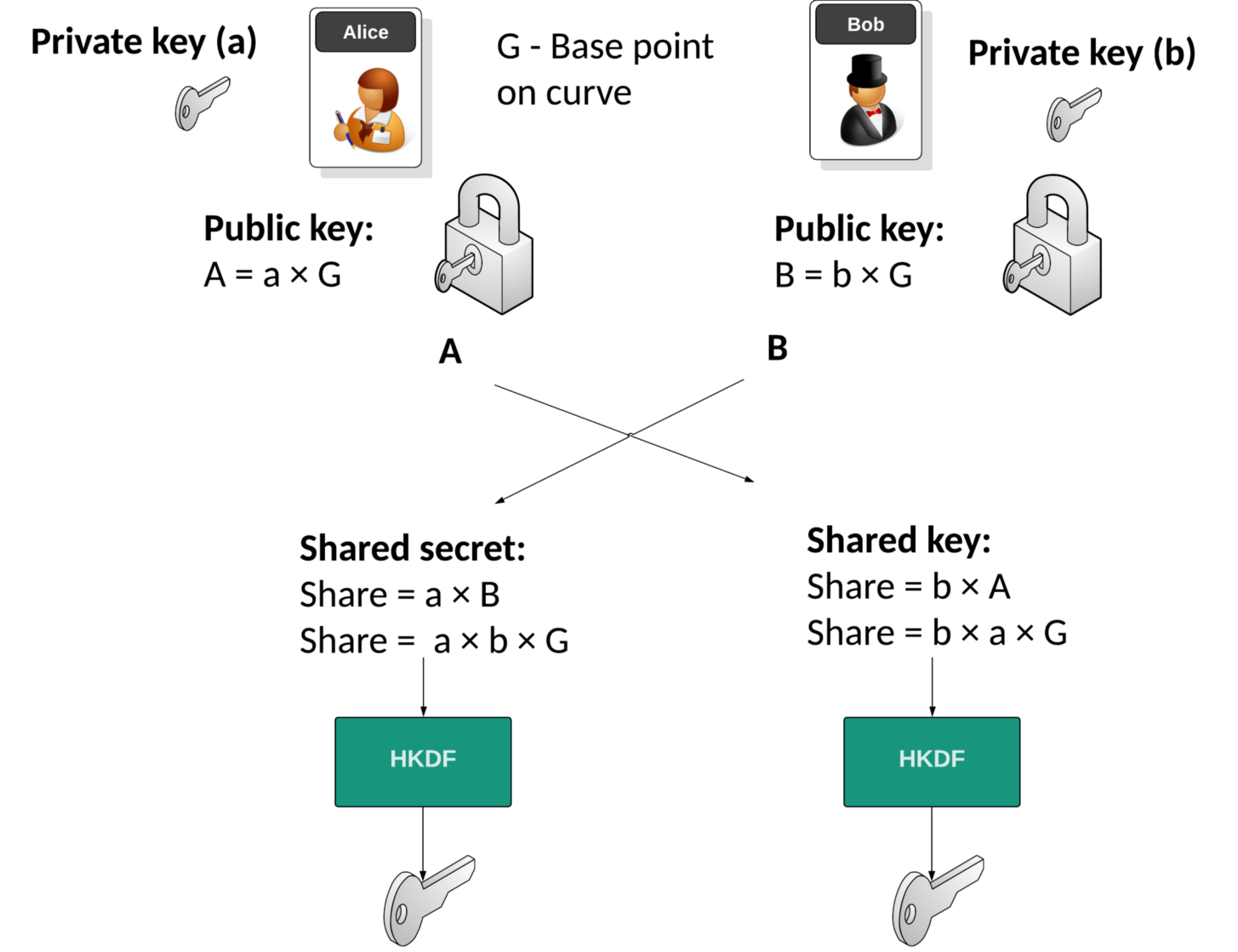
How to exchange a secret key over an insecure network (EC-Diffie-Hellman algorithm) | by Mikhail Karavaev | Level Up Coding

PDF) Implementation of Elliptic Curve Diffie-Hellman (ECDH) for Encoding Messeges Becomes a Point on the GF( ) 1*